Handshake is usually a term used to describe the transfer of confidential information between a computer or a device where there is a transfer of information like password , BSSID / MAC address etc and this information is in encrypted form known as a handshake.
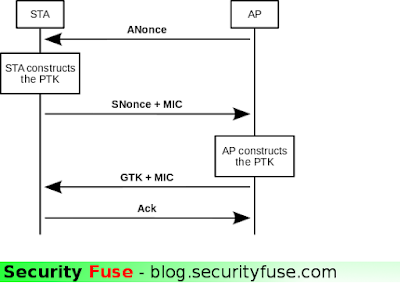
When there is a LAN or WAN network and a client or user , he or she sends a request to get connected to that network and the network is password protected now Network ask user or client to enter the password to get connected when he or she enters that password it is sent in encrypted form. moreover the same thing when users computer or device auto-connects itself with a network when the user have already authenticated himself and this step usually contain a four way transfer of data also known as 4 way handshake which contain encrypted information and hashes of password which user used to authorize himself.
There are few widely used encryption,s
- WEP - Wired Equivalent Privacy
- WPA - Wi-Fi Protected Access
- WPA2 - Wi-Fi Protected Access
- WPS PIN Authentication
WEP Encryption was indeed the first encryption ever used to authenticate the user over the network to insure the user privacy it uses a security algorithm of IEEE 802.11 and was introduced in September 1999 and contain 10 or 26 hexadecimal digits but nothing is perfect and as a result it was replaced by WPA encryption in 2004 because hacker,s were able to decrypt it easily.
WPA / WPA2 WiFi Protected Access , WPA was introduced in 2004 as discussed above as a replacement of WEP encryption. WPA is also considered as intermediate form because it combines some authentication features of WEP. WPA uses 256-bit keys.
How To Capture The Handshake
There are few ways to capture the handshake but we will only try to coverup the two common ways
- Using airodump-ng
- Using wifite
In airodump you will have to perform every single step manually but in wifite which is an automated script comes pre-loaded and ready to use in Kali Linux will perform all the steps itself and all you need to do is to assign him a target.
Make sure that you have a good WiFi Adapter which is enough for capturing the handshake and we will recommend you " Alpha AWUSO36 " which is perfect for such type of network penetration and testing.
Also there must be clients or users connected to their network before you can start capturing the network handshake because without clients or users there will be no exchange of Encrypted keys from client side to server side.
So lets start using the first method
airodump-ng
1. First you will need to enable your monitor mode for this you can type the command mentioned below
airmon-ng start wlan0wlan0 could be different in your case you can check it by typing " ifconfig "
Now moniter mode will be enabled and in my case it is enabled on " mon0 "
2. Now we will start a scan to check WiFi Network in our range by typing the command stated below
Clients who are connected are shown below the scan result i.e in the above picture you can see one client who,s BSSID is starting from 00 and ending with 91 and below the station. which displays BSSID or MAC of the client. You can also identify if anyone is connected or not by simply pressing a TAB button while scanning and it will highlight the clients who are connected to the network.
To capture the encrypted handshake type the command stated below in a new terminal
airodump-ng -c 6 --bssid 00:1D:7E:64:9A:7C --showack -w capture mon0In the above command change the channel number and BSSID and monitor interface with your,s
Channel Number after -c
BSSID after --bssid
monitor interface after capture " mon0 "
In which -w is the capture file name to save the handshake
Now it has started capturing and the only thing we need to do is to de-authenticate the client or user from the network so when he is de-authenticated his machine will try to re-connect to the network and in this way there will be a transfer of encrypted password and confidential data over the network and we can easily intercept it and capture the file in .cap as a handshake.
There are two common ways to disconnect the user or client from the network
- aireplay-ng
- mdk3
To disconnect users or clients from the network using aireplay type the command stated below
aireplay-ng -0 5 -a 00:1D:7E:64:9A:7C -c 00:25:D3:0B:71:15 mon0Again change few things with your,s as -a is the Access Point MAC address and -c is the client MAC address which is connected to the AP and monitor interface as mine is mon0 and leave the rest of the command.
Now if you succeeded in capturing a valid handshake by disconnecting the users from aireplay its great but if you failed you can try disconnecting from mdk3 because many of access points now a days have firewall which stops aireplay packets.
To disconnect users using mdk3 type
mdk3 mon0 d
Now it will start disconnecting all the clients or users in the range so once you see that your victim is disconnecting immediately stop to let him connect back to his network so you can capture the handshake.
This is how you can capture the handshake using the above method now lets move toward the second method which is capturing handshake using wifite an automated script.
Capture Handshake using Wifite
Wifite is a perfect automated script for launching attacks on WiFi networks and it is also used for capturing handshake. for this simply you type the command stated below.
wifiteNow wifite will start and it may ask you for monitor interface for this you can type the number of enabled monitor interface which it will display
Now it will list all the wifi networks in range all you have to do is to press " CTRL + C " after the scan and type the WiFi number which you want to attack and it will start capturing the handshake and will save it in the directory : /root/hs/ but if it start any other type of attack such as wps attack again you can press CTRL + C to move toward the next step which is Handshake capturing.
This is how you can capture handshake , we have demonstrated two methods and hope you will enjoy penetration and testing and also do share if you liked that article because sharing is caring.
Visitors should strictly follow the terms and conditions. The content provided on this page is the authority of Security Fuse and the content provided is only for educational purpose. Security Fuse is not responsible for any of the act caused by viewers after reading the content from *.securityfuse.com. our aim is to provide a quality information on Cyber Security and exploitation and the knowledge is only for peace and educational purpose.






Great job dude
ReplyDeleteCreating a network even at home is very easy. Only you need to buy a router and find a password before you are ready with a wireless network but your computers are vulnerable to attacks by hackers.
ReplyDeletedownload shareit app
hi
ReplyDeleteI have 9th devices in range of my computer & i try above method to all device ,only one device handshake captured out of 9 & i have try same method in all , but only one capture why???????
there is any reason or same else ??
is that a advance technology router ???
please answer me !
hi
ReplyDeletei use above method in 9 wifi network but only one handshake is capture plz help me what is reason here ,
Being a hacker without having knowledge of programming is just like a knife without sharpness
ReplyDeletewhen we use word knife
and any knife can kill
The easiest way to determine how many WiFi Access Points you require is to carry out a site survey. You'll need a WiFi router and a Laptop.www.electricalshop.net
ReplyDeleteNice Article, read now Haalim Episode 15 here.
ReplyDelete